Tunnelblick Ios App
In this episode we show you how to use single vpn server that you setup (from the previous episode) with multiple clients and we show you how to set it up on. OpenVPN Connect is the official full-featured iPhone/iPad VPN client for the OpenVPN Access Server, OpenVPN Cloud and OpenVPN Community, developed by OpenVPN Technologies, Inc. Features:. Easily import.ovpn profiles from iTunes, OpenVPN Access Server, OpenVPN Cloud or via a browser link.
The method to install OpenVPN on iOS is different on iOS 13 compared to previous versions. Unless you have updated to the latest iOS version, follow this guide instead.
1. Download OpenVPN Connect
The first thing you need to do in order to connect to OVPN is to install OpenVPN Connect for iOS.
2. Download the configuration you want
Tunnelblick App Apple
3. Open the downloaded configuration file
After you have downloaded the configuration you want, you will need to confirm the download by clicking on Download.
Click on the download button that appears in Safari.
Click on the configuration file that appears in the new modal.
Click on the share icon
A list of installed apps appear. Swipe as much to the right as possible until you see the option More
Scroll down in the list of suggestions until you find Copy to OpenVPN. Click on it.
OpenVPN Connect will now be opened. You might need to agree to some terms if it's the first time the app gets opened. Click on Agree.
4. Enter your OVPN credentials
The OpenVPN configuration profile can now be imported into the app by clicking on Add
Tunnelblick Android
Enter your OVPN account credentials. Click on Add in the upper right corner when you're done.
Tunnelblick For Ipad
Allow OpenVPN to create a VPN configuration by clicking on Allow.
Confirm the action by typing in your iPhone passcode.
5. Connect to OVPN
Connect by clicking on the grey toggle that appears next to the profile name.
Allow OpenVPN to enable VPN connections.
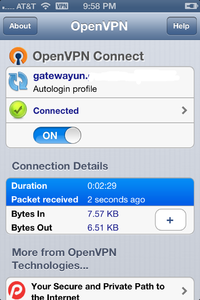
You should now be connected to OVPN and you will see
6. Finished
You should now be connected to OVPN and be able to browse the internet safely. To make sure everything was set up correctly, please check the dashboard to verify that you are connected.
-->
This article helps you configure OpenVPN ® Protocol clients.
Before you begin
Verify that you have completed the steps to configure OpenVPN for your VPN gateway. For details, see Configure OpenVPN for Azure VPN Gateway.
Windows clients
Download and install the OpenVPN client (version 2.4 or higher) from the official OpenVPN website.
Download the VPN profile for the gateway. This can be done from the Point-to-site configuration tab in the Azure portal, or 'New-AzVpnClientConfiguration' in PowerShell.
Unzip the profile. Next, open the vpnconfig.ovpn configuration file from the OpenVPN folder using Notepad.
Export the point-to-site client certificate you created and uploaded to your P2S configuration on the gateway. Use the following article links:
VPN Gateway instructions
Virtual WAN instructions
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your machine is one way. The profileinfo.txt file contains the private key and the thumbprint for the CA and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in Notepad. To get the thumbprint of the client (child) certificate, select the text (including and between)'-----BEGIN CERTIFICATE-----' and '-----END CERTIFICATE-----' for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Switch to the vpnconfig.ovpn file you opened in Notepad from step 3. Find the section shown below and replace everything between 'cert' and '/cert'.
Open the profileinfo.txt in Notepad. To get the private key, select the text (including and between) '-----BEGIN PRIVATE KEY-----' and '-----END PRIVATE KEY-----' and copy it.
Go back to the vpnconfig.ovpn file in Notepad and find this section. Paste the private key replacing everything between and 'key' and '/key'.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
Copy the vpnconfig.ovpn file to C:Program FilesOpenVPNconfig folder.
Right-click the OpenVPN icon in the system tray and click connect.
Mac clients
Download and install an OpenVPN client, such as TunnelBlick.
Download the VPN profile for the gateway. This can be done from the point-to-site configuration tab in the Azure portal, or by using 'New-AzVpnClientConfiguration' in PowerShell.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can simply open the .cer file and copy over the base64 key between the certificate headers. Use the following article links for information about how to export a certificate to get the encoded public key:
VPN Gateway instructions
Virtual WAN instructions
Fill in the private key section with the P2S client certificate private key in base64. See the Export your private key on the OpenVPN site for information about how to extract a private key.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
Double-click the profile file to create the profile in Tunnelblick.
Launch Tunnelblick from the applications folder.
Click on the Tunnelblick icon in the system tray and pick connect.
Important
Only iOS 11.0 and above and MacOS 10.13 and above are supported with OpenVPN protocol.
iOS clients
Install the OpenVPN client (version 2.4 or higher) from the App store.
Download the VPN profile for the gateway. This can be done from the point-to-site configuration tab in the Azure portal, or by using 'New-AzVpnClientConfiguration' in PowerShell.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can simply open the .cer file and copy over the base64 key between the certificate headers. Use the following article links for information about how to export a certificate to get the encoded public key:
VPN Gateway instructions
Virtual WAN instructions
Fill in the private key section with the P2S client certificate private key in base64. See Export your private key on the OpenVPN site for information about how to extract a private key.
Do not change any other fields.
E-mail the profile file (.ovpn) to your email account that is configured in the mail app on your iPhone.
Open the e-mail in the mail app on the iPhone, and tap the attached file
Tap on More if you do not see Copy to OpenVPN option
Tap on Copy to OpenVPN
Tap on ADD in the Import Profile page
Tap on ADD in the Imported Profile page
Launch the OpenVPN app and slide the switch in the Profile page right to connect
Linux clients
Open a new Terminal session. You can open a new session by pressing 'Ctrl + Alt + t' at the same time.
Enter the following command to install needed components:
Download the VPN profile for the gateway. This can be done from the Point-to-site configuration tab in the Azure portal.
Export the P2S client certificate you created and uploaded to your P2S configuration on the gateway. Use the following article links:
VPN Gateway instructions
Virtual WAN instructions
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your computer is one way.
The profileinfo.txt file will contain the private key and the thumbprint for the CA, and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in a text editor. To get the thumbprint of the client (child) certificate, select the text including and between '-----BEGIN CERTIFICATE-----' and '-----END CERTIFICATE-----' for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Open the vpnconfig.ovpn file and find the section shown below. Replace everything between the and 'cert' and '/cert'.
Open the profileinfo.txt in a text editor. To get the private key, select the text including and between '-----BEGIN PRIVATE KEY-----' and '-----END PRIVATE KEY-----' and copy it.
Open the vpnconfig.ovpn file in a text editor and find this section. Paste the private key replacing everything between and 'key' and '/key'.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
To connect using the command line, type the following command:
To connect using the GUI, go to system settings.
Click + to add a new VPN connection.
Under Add VPN, pick Import from file…
Browse to the profile file and double-click or pick Open.
Click Add on the Add VPN window.
You can connect by turning the VPN ON on the Network Settings page, or under the network icon in the system tray.
Next steps
If you want the VPN clients to be able to access resources in another VNet, then follow the instructions on the VNet-to-VNet article to set up a vnet-to-vnet connection. Be sure to enable BGP on the gateways and the connections, otherwise traffic will not flow.
'OpenVPN' is a trademark of OpenVPN Inc.
