Nmmhkkegccagdldgiimedpiccmgmieda
- Google Chrome Games
- Chrome Extension Nmmhkkegccagdldgiimedpiccmgmieda
- Nmmhkkegccagdldgiimedpiccmgmieda Google Wallet
Automated Malware Analysis - Joe Sandbox IOC Report. Signature Hits: Behavior Group: Mitre Attack: Antivirus / Scanner detection for submitted sample. further weirdness is that the icon for the extension matches that of the google wallet logo, so im guesssing it might be an official google extension, though its weird that i cant find any documentation for it, and that it turns up a warning on the antimalware scanner - You received this message because you are subscribed to the Google Groups 'Chromium-extensions' group.
Quest KACE K1000 (Former Dell Product), allows you to create “customized” inventory rules that provide flexibility to run commands, whether through standard command prompt, or other methods.
For this particular use case, we’re trying to identify what Chrome extensions are installed in our non-domain endpoints that we’re managing. If you are dealing with domain-joined systems, I’d recommend managing these extensions via Google Chrome’s GPO which can be found in my past article.
If you don’t use KACE K1000 in your environment, you can still follow the article and later skip to the “For non-KACE users” section to accomplish the same thing.
Within KACE we’re going to create a custom inventory rule to return the extensions found under my user appdata directory: C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions
I found the easiest way to do this is to use the dir command within command prompt, with the /b syntax.
dir /b “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions” which returns the following:
Reference for Dir:
| /b | Use this option to show the dir results using “bare” format, which removes the typical header and footer information, as well as all the details on each item, leaving only the directory name or file name and extension. |
The equivalent of powershell is this:
Get-ChildItem -Path “$($env:LOCALAPPDATA)GoogleChromeUser DataDefaultExtensions” -Name
Within Kace, create a custom inventory rule and call it “Google Chrome Extensions”
Navigate to Inventory > Software > Choose Action > New
provide a script name: Google Chrome Extensions
Highlight all of your Windows OS under Supported Operating Systems
Enter the following as the custom inventory rule:
ShellCommandTextReturn(dir /b “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions”)
Save it!
This will run that command on each endpoint that matches that path and will save the output to the KACE database. Note: This is assuming that your non-domain systems are using the same username. If your usernames are all different throughout the environment, I don’t think this will work. I played around with dir /b “%LOCALAPPDATA%GoogleChromeUser DataDefaultExtensions” but this did not work. I’m assuming it’s because the KACE agent is running as SYSTEM user context.

Moving on, you should see the list of extensions when you look at custom inventory rules results when looking up an endpoint.
Identifying Extensions:
Google chrome comes with certain extensions by default, in addition there are legitimate extensions such as Adobe PDF readers, or anti-virus extensions added by legitimate products. I spent some time identifying the known extensions via Google Chrome Extensions site; Although some extensions follow an old ID convention or the Google URL store has changed.
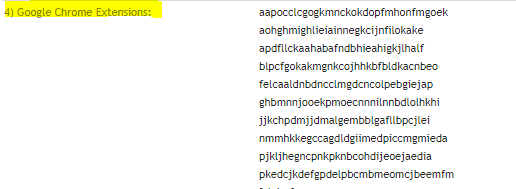
Here they are:
| Extension Name | Extension ID |
| Google Slides | aapocclcgogkmnckokdopfmhonfmgoek |
| Google Docs | aohghmighlieiainnegkcijnfilokake |
| Google Calendar #old extension | ejjicmeblgpmajnghnpcppodonldlgfn |
| Google Docs | ghbmnnjooekpmoecnnnilnnbdlolhkhi |
| Google Drive | apdfllckaahabafndbhieahigkjlhalf |
| Youtube | blpcfgokakmgnkcojhhkbfbldkacnbeo |
| Google Sheets | felcaaldnbdncclmgdcncolpebgiejap |
| Google Chrome Web Store | nmmhkkegccagdldgiimedpiccmgmieda |
| Gmail | pjkljhegncpnkpknbcohdijeoejaedia |
| Chromecast | pkedcjkdefgpdelpbcmbmeomcjbeemfm |
| Google Search | coobgpohoikkiipiblmjeljniedjpjpf |
| Google Translate | aapbdbdomjkkjkaonfhkkikfgjllcleb |
I like interacting with the KACE database directly via Mysql Workbench; therefore, I created a SQL script to easily identify the known extensions when creating reports. This made it easy to identify the unknown extensions and also spotting nefarious extensions that shouldn’t be running in the environment:
Note: this assumes that you created the custom inventory software rule and named it “Google Chrome Extensions”.
Here’s the SQL script which will allow you to create an easy-to-read report:
Creating KACE Report for Google Chrome Extensions
Navigate to Reporting > Reports > Select the Drop down menu and select New (SQL)
Provide a title and paste the SQL code provided earlier:
Save it.
Next, run the Report
You should see a report of your endpoints along with the extensions:
As you can see, it’ll be easy to identify unknown extensions.
Although it’s nice that we have visibility over our endpoints, this doesn’t stop the malicious extensions installed from running. The next step is to eradicate those extensions.
Removing unwanted Google Chrome Extensions

Now that we have a good idea of the known good extensions, we can remove all unwanted extensions. To accomplish this, I wrote a Powershell Script and also briefly modified a well known extension written by “bellows” at Spiceworks that removes Google Chrome extensions.
The first Powershell script “GoogleChromeExtensions.ps1” will query the Extensions directory and will exclude the “known expected” extensions and will return only the extensions not found under this list. The list of “unknown or unwanted” extensions will then be passed on to the “Get-ChromeExtensions.ps1” Powershell Script that will start removing each one at a time. This script will remove the extension folder contents for this path, and will also remove registry entries under HKCUSOFTWARE for those extensions.
Here’s the “Get-ChromeExtensions.ps1” script. The only thing I modified was the path to the extensions as Dell KACE will run as SYSTEM and the script won’t work if you don’t deploy it this way. (Note: You may also run scripts as the user context, but I didn’t test this route).
The Modified line is this one: $extension_folders = Get-ChildItem -Path “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions”
Deploying the script via KACE
Navigate to Scripts > Choose Action > New
Provide a name for the script and make sure you “enable” it.
- Select the Operating system to “Microsoft Windows”.
- Windows run As “Local System”
- Check box for “Allow run without a logged-in user”
- Upload dependencies (GoogleChromeExtensions.ps1) & (Get-ChromeExtensions.ps1)
Under the Tasks section:
On Success : Run a batch file
Provide a script name and paste the following:
powershell.exe powershell.exe -ExecutionPolicy UnRestricted -File .GoogleChromeExtensions.ps1
Save changes, and deploy!
For non-KACE users
You can run these Powershell scripts without specifying a user, and just grabbing the current logged in user via the %LOCALAPPDATA% variable. Ensure you modify the script with other expected extensions or just remove them all!
Here’s the scripts:
Google Chrome Games
and you may use the original “Get-ChromeExtensions.ps1” script along with the one I created which should accomplish the same thing. Easy as 1,2,3.
Conclusion
As mentioned earlier, the scripts deployed will remove unwanted extensions from the provided file path and registry keys; however the extension itself WILL NOT be removed from the Google Chrome browser. When you re-launch the web browser, the folders will re-appear; however, they wont’ have any content and the extension will not be functional. If you browse to the extensions section of Chrome, you will see the extensions with a status of “This extension may have been corrupted” and thus will not be functional as seen in the image below:
Although we’d like to have the extension completely removed from the user’s visibility, this is the next best thing. To my knowledge there isn’t a way to remove the extensions besides having the user do it manually (correct me if I’m wrong, as there might be a better way). The user may always re-install the extensions; however, you can always have an ongoing-job to continue deleting them.
Thanks for reading! Constructive feedback is always appreciated!
What is WebDiscover?
WebDiscover is a browser that is deservedly treated as Potentially Unwanted Application. It established this reputation because of its unauthorized method of installation and the malicious effects it has. The browser itself is based on Google Chromium project and is pushed for as a more functional alternative to popular web browsers. By the developer’s word, WebDiscover would expand the horizons of browsing. Well, WebDIscover really has features that other browsers don’t, but they hardly can be called good for you or your system. These include adding a search bar to your desktop that will be shown above all applications and if used can provide unpredictable results – sometimes it would give you relevant results from trustworthy sources, and sometimes you will be redirected to suspicious sites. Within the browser, you will be seeing annoying ads popping all over the pages. Since using the browser doesn’t bring anything beneficial you should uninstall WebDiscover and use one of the free browsers with a good reputation.
How WebDiscover got installed on your computer?
The installation of WebDiscover can be initiated by various methods. Among them, the method of bundling the browser with some freeware is the most frequent. In installation wizards, it is presented as a free download, which many users accept as they consider the application to be of use. It is encouraged by the false description that dignifies the browser to be an advantageous program. Otherwise, they do not notice the malware at all, as it is intently hidden and can be only detected if Advanced mode of setup is chosen.
How to remove WebDiscover?
We should warn you that performing some of the steps may require above-average skills, so, if you don’t feel experienced enough, you may apply to the automatic removal tool.
Performing an antimalware scan with Norton would automatically search out and delete all elements related to WebDiscover. It is not only the easiest way to eliminate WebDiscover, but also the safest and most assuring one.

Steps of WebDiscover manual removal
Uninstall WebDiscover from Control Panel
You could have downloaded the program yourself but, as it was stated before, more likely that the rogue application appeared on your system brought with other software. So, to get rid of WebDiscover you need to call to memory what you have installed recently.
How to uninstall WebDiscover from Windows XP
- Click the Start button and open Control Panel
- Go to Add or Remove Programs
- Find the application related to WebDiscover and click Uninstall
How to uninstall WebDiscover from Windows 7/Vista
- Click the Start button and open Control Panel
- Go to Uninstall Program
- Find the application related to WebDiscover and click Uninstall
How to uninstall WebDiscover from Windows 8/8.1
- Right-click the menu icon in left bottom corner
- Choose Control Panel
- Select the Uninstall Program line
- Uninstall the application related to WebDiscover
How to uninstall WebDiscover from Windows 10
- Press Win+X to open Windows Power menu
- Click Control Panel
- Choose Uninstall a Program
- Select the application related to WebDiscover and remove it
If you experience problems with removing WebDiscover from Control Panel: there is no such title on the list, or you receive an error preventing you from deleting the application, see the article dedicated to this issue.
Read what to do if program won’t uninstall from Control Panel
Delete files and registry entries added by WebDiscover
Sometimes removal via Control Panel is not enough since the built-in application can leave some files. So, you need to find all of the following items and delete them.
Remove WebDiscover files and folders:
Program FilesWebDiscoverBrowser
config.json
DelayedStart.lnk
isa.dll
Start.lnk
unins000.dat
unins000.exe
wdsvc2.exe
41.0.2272.74.manifest
chrome.dll
chrome.exe
chrome_100_percent.pak
chrome_200_percent.pak
chrome_child.dll
chrome_elf.dll
d3dcompiler_47.dll
debug.log
delegate_execute.exe
ffmpegsumo.dll
icudtl.dat
isa.dll
libEGL.dll
libexif.dll
libGLESv2.dll
master_preferences
metro_driver.dll
nacl_irt_x86_32.nexe
nacl_irt_x86_64.nexe
nacl64.exe
pdf.dll
resources.pak
external_extensions.json
RightCoupon.crx
theme.crx
webdiscover_helper.crx
Users{username}AppDataLocalWebDiscoverBrowserUser DataFirst Run
Users{username}AppDataLocalWebDiscoverBrowserUser DataLocal State
Users{username}AppDataLocalWebDiscoverBrowserUser Datalockfile
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Bloom
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Bloom Prefix Set
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Cookies
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Cookies-journal
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Csd Whitelist'
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Download
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Download WhitelistUsers{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing Extension Blacklist
Users{username}AppDataLocalWebDiscoverBrowserUser DataSafe Browsing IP Blacklist
Users{username}AppDataLocalWebDiscoverBrowserUser DataCaps
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefault
ChromeDWriteFontCache
Current Session
Current Tabs
Favicons
Favicons-journal
Google Profile.ico
History
History-journal
Preferences
README
Secure Preferences
Shortcuts
Shortcuts-journal
Top Sites
Top Sites-journal
Visited Links
Web Data
Web Data-journal
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultCache
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtension Rules
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtension State
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtensionsckpkimghacdmjngcijkahobkblcdkoma1.0_0
background.js
manifest.json
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtensionsnmmhkkegccagdldgiimedpiccmgmieda0.1.2.0_0
craw_background.js
craw_window.js
manifest.json
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtensionsnmmhkkegccagdldgiimedpiccmgmieda0.1.2.0_0_locales
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtensionsppfloidffgmiommjibgmbbabccaaajff1.0.0_0
manifest.json
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultExtensionsppfloidffgmiommjibgmbbabccaaajff1.0.0_0js
inject.js
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultJumpListIcons
E0C5.tmp
E0C6.tmp
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultJumpListIconsOld
6B83.tmp
6B84.tmp
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultLocal Extension Settingspafkbggdmjlpgkdkcbjmhmfcdpncadgh
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultLocal Storage
chrome-extension_pafkbggdmjlpgkdkcbjmhmfcdpncadgh_0.localstorage
chrome-extension_pafkbggdmjlpgkdkcbjmhmfcdpncadgh_0.localstorage-journal
Users{username}AppDataLocalWebDiscoverBrowserUser DataDefaultSession Storage
Users{username}AppDataLocalWebDiscoverBrowserUser DataEVWhitelist
Users{username}AppDataLocalWebDiscoverBrowserUser Datapnacl
UsersPublicDesktop
WebDiscover Browser.lnk
WebDiscover Browser Launch Task
Remove WebDiscover registry entries:
Chrome Extension Nmmhkkegccagdldgiimedpiccmgmieda

Nmmhkkegccagdldgiimedpiccmgmieda Google Wallet
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstall{fd13f4a2-b0d8-4cad-9ccf-d4128eaf25ff}_is1
HKEY_LOCAL_MACHINESOFTWAREWebDiscoverBrowser
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesWebDiscover Browser Startup Service
HKEY_CURRENT_USERSoftwareChromiumBLBeacon
HKEY_CURRENT_USERSoftwareChromiumBLFinchList
HKEY_CURRENT_USERSoftwareChromiumBrowserCrashDumpAttempts
HKEY_CURRENT_USERSoftwareChromiumBrowserExitCodes
HKEY_CURRENT_USERSoftwareChromiumBrowserExitCodes3028-13096392205660309
HKEY_CURRENT_USERSoftwareChromiumStabilityMetrics
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
HKEY_CURRENT_USERSoftwareWebDiscoverBrowser
HKEY_CURRENT_USERSoftwareWebDiscoverBrowserBrowser
